Azure Sentinel is a cloud-native security information and event manager (SIEM) platform that uses built-in AI to help analyse large volumes of data across your enterprise. It makes it easy to collect security data across your entire hybrid organization from devices, users, apps or servers within the cloud or on-premise.
When linked into all of your domain controller's security logs, it offers simple and powerful queries using the Kusto Query Language to quickly find out events such as who deleted or disabled an active directory user account.
This guide assumes every one of your Domain Controllers has the Microsoft Monitoring Agent setup and point to the same Azure Sentinel Workspace using the Security Events data connector in Sentinel.
Within Sentinel select General > Logs then paste one of the following queries and adapt as per your requirements.
The following query shows who deleted the active directory account called john.smith within the last 24 hours,
SecurityEvent
| where EventID == 4726
| where TargetUserName == 'john.smith'
| where TimeGenerated > ago(24h)To show active directory accounts disabled during a certain time window,
SecurityEvent
| where EventID == 4725
| where TimeGenerated between(datetime("2021-01-01 01:00:00") .. datetime("2021-01-05 01:00:00")) 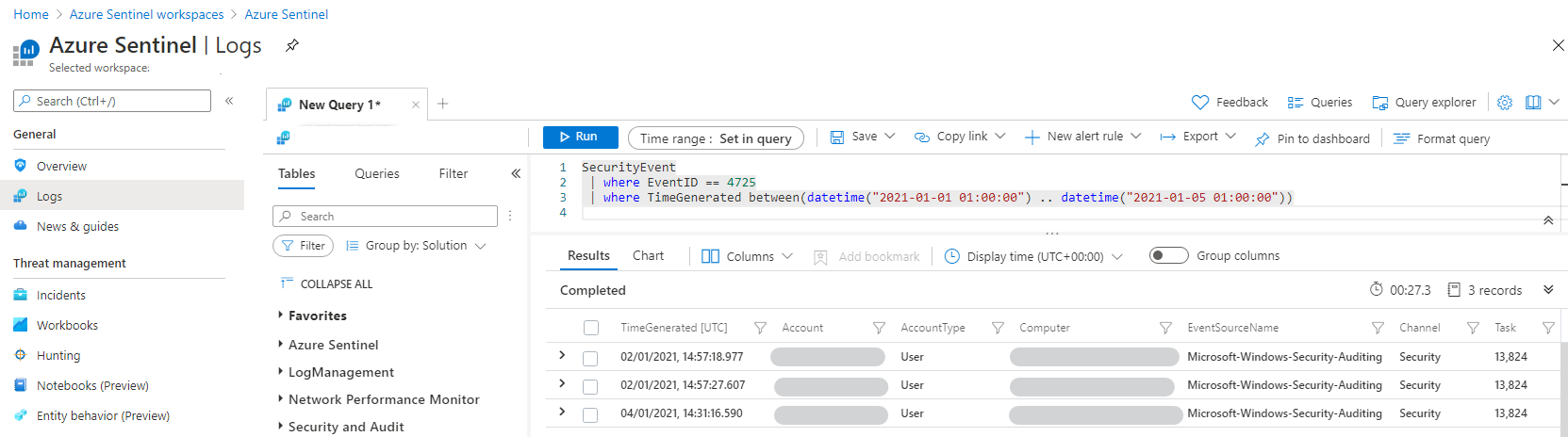
To show active directory accounts that have been enabled in the past 5 days,
SecurityEvent
| where EventID == 4722
| where TimeGenerated > ago(5d)To develop your filters further, see the quick reference on the Kusto Query Language at https://docs.microsoft.com/en-us/azure/data-explorer/kql-quick-reference